API Security in ASP.NET Core
- .Net
- November 05, 2024
-
API Security in ASP.NET Core
Introduction:
API security is a critical aspect of modern web application development, especially with the increasing adoption of APIs for data exchange between client applications and servers. APIs (Application Programming Interfaces) play a crucial role in enabling communication between different software systems. However, with the increasing reliance on APIs for data exchange, ensuring their security becomes paramount. API security encompasses a range of practices and techniques aimed at protecting APIs from unauthorized access, data breaches, and other security threats. In this blog post, we'll explore various methods for securing APIs in ASP.NET Core, along with their advantages, disadvantages, and practical examples.
Methods for API Security in ASP.NET Core:
1. JWT Authentication
JWT (JSON Web Tokens) authentication is a popular method for securing APIs by issuing tokens to authenticated users. JSON Web Tokens (JWT) are a compact, JSON Web Tokens (JWT) are a compact, URL-safe means of representing claims to be transferred between two parties. These tokens are encoded and signed JSON objects that contain claims, which are statements about an entity (typically the user) and additional data. JWT tokens consist of three parts: a header, a payload, and a signature. JWT authentication involves issuing tokens to authenticated users, which are then sent with each request to authenticate the user. When a user logs in or authenticates with the server, a JWT token is generated and sent back to the client. The client then includes this token in subsequent requests to access protected resources. Upon receiving a request with a JWT token, the server validates the token's signature and claims to ensure its authenticity and integrity. This validation includes verifying the token's issuer, audience, expiration time, and signature.Advantages of JWT Authentication:
Stateless: JWT tokens contain all necessary user information, eliminating the need for server-side session storage.
Scalable: Since JWT tokens are self-contained, they can be easily distributed across multiple servers or microservices.
Decentralized: Authentication can be performed by any service that has access to the token signing key.
Disadvantages of JWT Authentication:
Token size: JWT tokens may become large if they contain extensive user information, potentially impacting network performance.
Lack of revocation: JWT tokens cannot be revoked once issued, making it challenging to implement logout functionality.
Maintenance and Updates: Keeping API security measures up-to-date requires ongoing maintenance and updates, adding to the overall development and operational overhead.
JWT Authentication Example:
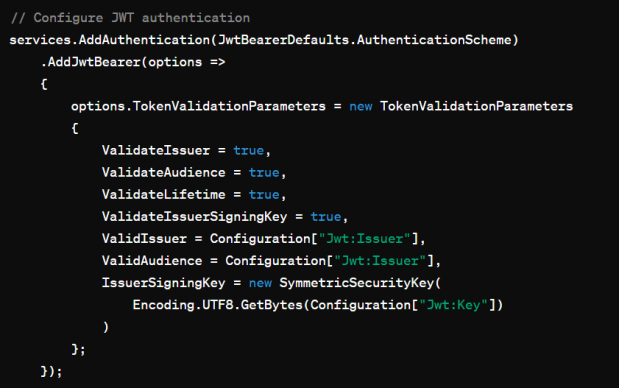
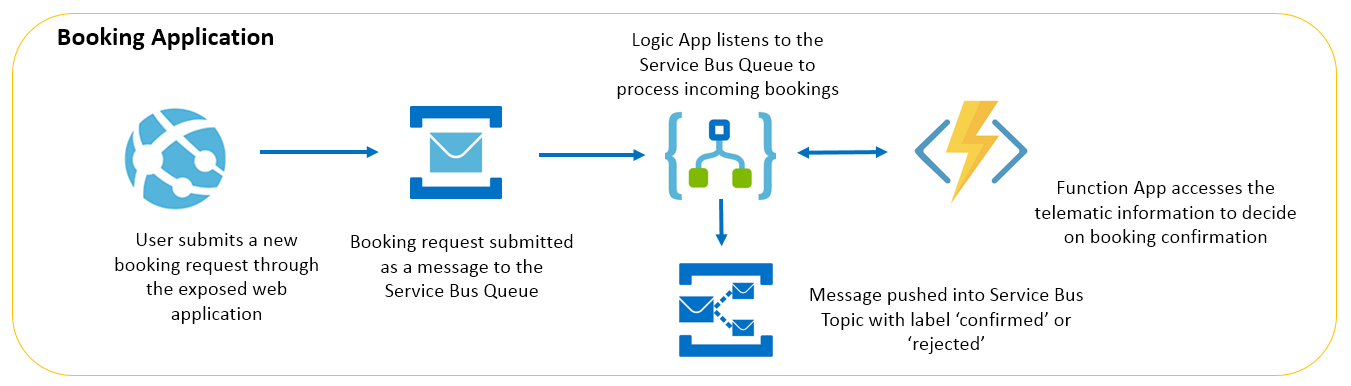
In this example, we configure JWT authentication for ASP.NET Core. We specify the token validation parameters, including validation of the issuer, audience, lifetime, and the issuer's signing key. The configuration is retrieved from the application's configuration file (appsettings.json), where the JWT issuer, audience, and key are defined.
2. API Key Authentication
API key authentication is a simple mechanism for securing APIs by issuing unique API keys to clients. Clients include their API key in requests to authenticate themselves with the server. The server validates the API key against a pre-configured set of keys to grant access to protected resources. API key authentication has limitations. Securing API keys requires proper secret management practices, including encryption, secure storage, and access control, to prevent unauthorized access and exposure.
Advantages of API Key Authentication:
Simplicity: API key authentication is straightforward to implement and requires minimal setup.
Rate Limiting: API keys can be used for rate limiting and enforcing quotas on API usage, preventing abuse and ensuring fair usage of resources.
Scoped Access: API keys can be scoped to specific functionalities or resources, allowing fine-grained access control based on the client's requirements.
Disadvantages of API Key Authentication:
Lack of User Identity: API keys do not provide user identity information, limiting their applicability for user-specific operations.
Security Risks: API keys can be exposed if not handled securely, leading to potential unauthorized access.
Limited Authentication Options: API key authentication offers limited authentication options compared to more robust methods like OAuth 2.0 and OpenID Connect, potentially limiting the flexibility of authentication mechanisms.
API Key Authentication Example:
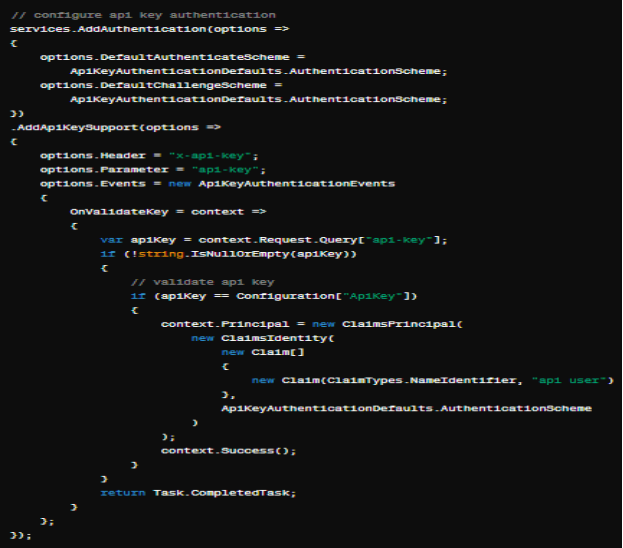
In this example, we configure API key authentication for ASP.NET Core. We specify the header and query parameter names used for API key authentication. The ‘OnValidateKey‘event handler is used to validate the API key against a pre-configured value stored in the application's configuration file appsettings.json. If the API key is valid, we create a claims principal representing the authenticated user and set it in the authentication context.
Start Your Data Journey Today With MSAInfotech
Take the first step towards data-led growth by partnering with MSA Infotech. Whether you seek tailored solutions or expert consultation, we are here to help you harness the power of data for your business. Contact us today and let’s embark on this transformative data adventure together. Get a free consultation today!

We utilize data to transform ourselves, our clients, and the world.

Partnership with leading data platforms and certified talents